Hi,
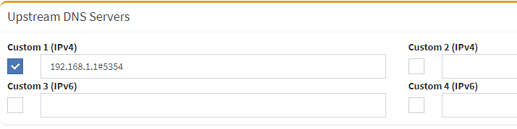
on my router I have ISP dns disabled, run an unbound instance on it (which uses mullvad dns over tls as upstream) and the router is set to use the unbound resolver as upstream on 127.0.0.1:5354. After I added pi-hole to my network I set the pi-hole to use the unbound on router as upstream (192.168.1.1#5354) too and set the dhcp on router to serve the pi-hole as dns server.
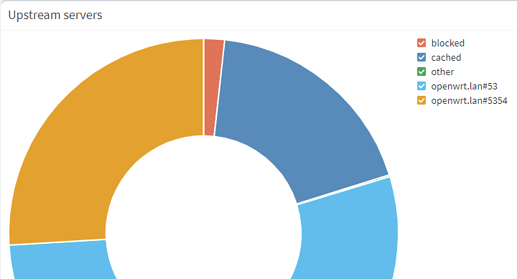
Everything works ok but I notice the pihole keeps resolving from 192.168.1.1:53 alongside 192.168.1.1:5354 even though 192.168.1.1#5354 is the single upstream defined for pi-hole. Is this because of the conditional forwarding when the pi-hole resolves the hostnames?
and this is the docker-compose.yml:
version: "3"
# https://github.com/pi-hole/docker-pi-hole/blob/master/README.md
services:
pihole:
container_name: pihole
hostname: pihole1-docker
image: pihole/pihole:latest
# privileged: true
# For DHCP it is recommended to remove these ports and instead add: network_mode: "host"
# network_mode: "host"
ports:
- "53:53/tcp"
- "53:53/udp"
- "67:67/udp"
- "80:80/tcp"
# - "443:443/tcp"
environment:
TZ: ${TZ}
WEBPASSWORD: ${PIHOLE_PASSWD}
PIHOLE_DNS_: ${DNS_1}
REV_SERVER: ${COND_FORWARD}
REV_SERVER_TARGET: ${ROUTER_IP}
REV_SERVER_DOMAIN: ${ROUTER_DOMAIN}
REV_SERVER_CIDR: ${ROUTER_REVERSE}
ServerIP: ${SERVER_IP}
# ServerIPv6: ${SERVER_IP6}
VIRTUAL_HOST: ${V_HOST}
# Volumes store your data between container upgrades
volumes:
- './etc-pihole/:/etc/pihole/'
- './etc-dnsmasq.d/:/etc/dnsmasq.d/'
# run `touch ./var-log/pihole.log` first unless you like errors
# - './var-log/pihole.log:/var/log/pihole.log'
cap_add:
- NET_ADMIN
- SYS_NICE # needed for negative nice
restart: unless-stopped
and the .env:
PIHOLE_PASSWD=[REDACTED]
TZ=Europe/London
DNS_1="192.168.1.1#5354"
COND_FORWARD=true
ROUTER_DOMAIN=lan
ROUTER_IP=192.168.1.1
ROUTER_REVERSE=192.168.1.0/24
SERVER_IP=192.168.1.101
SERVER_IP6=
V_HOST=pi-hole
FTLCONF_REPLY_ADDR4=192.168.1.101