well, 192.168.1.1 is the router, so I suppose is okay as it should redirect to the pi
the google ones were set before I changed the ones on the router, so yes, they have been recently (or so) changed
Let's try to verify that those servers aren't used anymore:
Run from a terminal on your Pi-hole machine, what is the output of:
dig +short chaos txt servers.bind
pi@raspberrypi:~ $ dig +short chaos txt servers.bind
"1.0.0.1#53 155 0" "1.1.1.1#53 84 0"
Ok, that shows the additional servers not being used.
How did you configure your router to make use of Pi-hole?
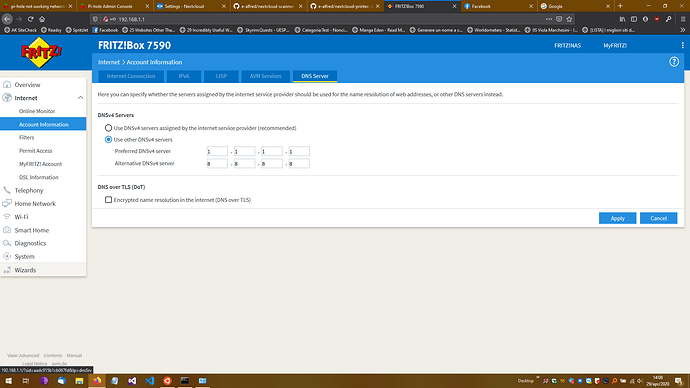
a) upstream DNS server ( Internet | Zugangsdaten | DNS-Server in a German FritzBox),
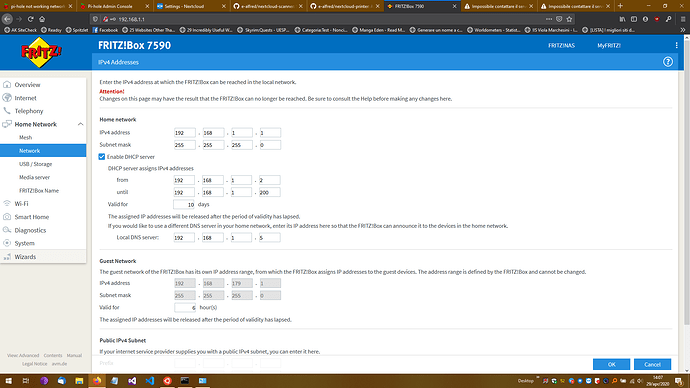
b) local DNS server ( Heimnetz| Netzwerk | Netzwerkeinstellungen | IPv4-Adressen )
c) both?
only the first one was configured, but even after configuring the "local DNS server" to 192.168.1.5 it doesn't change anything, there's no connection to any site and also the results of the previous commands are the same
C:\Users\erics>nslookup pi.hole
Server: fritz.box
Address: 192.168.1.1
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
*** Time expired for request to fritz.box
C:\Users\erics>nslookup pi.hole 192.168.1.5
DNS request timed out.
timeout was 2 seconds.
Server: UnKnown
Address: 192.168.1.5
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
*** Time expired for request to Unknown
C:\Users\erics>nslookup pi.hole
Server: fritz.box
Address: 192.168.1.1
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
*** Time expired for request to fritz.box
C:\Users\erics>nslookup pi-hole.net 1.1.1.1
Server: one.one.one.one
Address: 1.1.1.1
Reply from non authoritative server:
Name: pi-hole.net
Addresses: 2604:a880:400:d0::1071:1
206.189.252.21
If you have successfully configured Pi-hole as local DNS (option b), there is no immediate need for employing option a) also.
Your timeouts could suggest that you somehow configured a DNS loop, which would be the case if your router ask Pi-hole for upstream DNS resolution, while Pi-hole is configured to use your router as usptream at the same time.
Try switching your router's upstream DNS back to ISP default or any other public DNS sefrver, if you prefer.
Your local clients will start using Pi-hole as distribituted by DHCP only once their DHCP lease renews (FB defaults to 10 days here) or when they disconnect and reconnect to your network (e.g. by switching off WiFi or by power-cycling each device, or rebooting your FB ( System | Sicherung | Neustart - sorry for German, can't find an English translation for this).
You can verify that Pi-hole is used for DNS:
A plain nslookup flurry.com should return your Pi-hole's Server name and IP Address in its first two lines.
still I cannot open any website and none of the devices connected to the network seem to go throught the pi-hole
I'm not using the pi-hole as DHCP but I should be able to at least open something like google.com, instead everything stops in the whole network (meaning that the change in DNS server inside the router takes place immediately)
C:\Users\erics>nslookup flurry.com
DNS request timed out.
timeout was 2 seconds.
Server: UnKnown
Address: 192.168.1.5
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
*** Time expired for the request to UnKnown
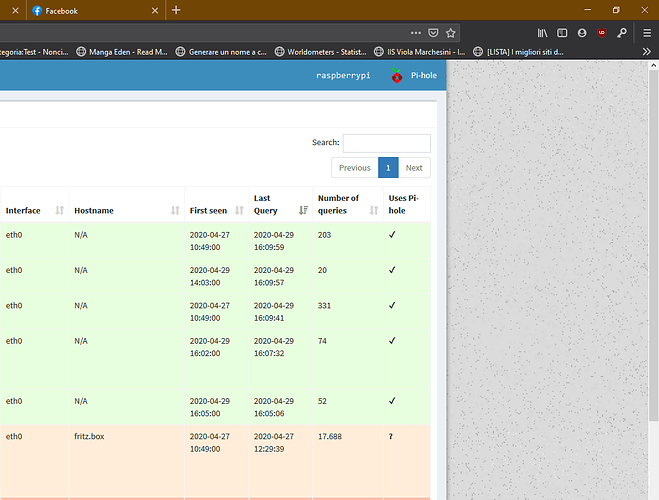
Your screenshots look ok, and nslookup shows your client is now using Pi-hole's intended IP address.
Let's check whether Pi-hole has actually established hold of that 192.168.1.5 address correctly.
Executed on your Pi-hole machine, what's the output of:
ip -4 address show
pi@raspberrypi:~ $ ip -4 address show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
inet 192.168.1.5/24 brd 192.168.1.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
3: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
inet 192.168.1.11/24 brd 192.168.1.255 scope global dynamic noprefixroute wlan0
valid_lft 855249sec preferred_lft 747249sec
4: br-dfc13dd69394: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
inet 172.18.0.1/16 brd 172.18.255.255 scope global br-dfc13dd69394
valid_lft forever preferred_lft forever
5: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
That reveals 192.168.1.5 is correctly bound to just one network interface, so that's good - no double address issues that sometimes occur when switching from LAN to WiFi.
It seems you are running Docker on your Pi-hole machine.
Are you running your Pi-hole as a Docker container?
No, I uninstalled docker some days ago as I was trying to make pihole work through homelabos without success. Instead I chose the direct installation to avoid any kind of problem. I've just removed the docker0 interface and the one before it as they were totally useless.
Good to know, since Docker may or may not introduce connectivity problems on its own that won't show up in a debug log.
Do nslookup commands work when run directly on your Pi-hole machine?
nslookup pi.hole
nslookup flurry.com
pi@raspberrypi:~ $ nslookup pi.hole
Server: 127.0.0.1
Address: 127.0.0.1#53
Name: pi.hole
Address: 192.168.1.5
pi@raspberrypi:~ $ nslookup flurry.com
Server: 127.0.0.1
Address: 127.0.0.1#53
Name: flurry.com
Address: 0.0.0.0
Name: flurry.com
Address: ::
So this shows that Pi-hole by itself is able to correctly resolve and block DNS requests.
Do you run a firewall on your Pi-hole machine that would block DNS ports from receiving requests?
Oh god I feel so dumb
I have ufw configured on my pihole machine, bu I thought the rules would be installed with the one-command installation
I checked and that was not the case, so I copied the commands from the page you linked and executed them as sudo and now it works everything, also every device I rebooted since the change is listed as working correctly even if the DHCP server is on the router
I tried loading some websites and MAN! THAT'S IMPRESSIVE! It's a lot faster than having UBlock Origin or similar add-ons. Do you think these add-ons are still necessary/useful with pihole?
Thank you very much for your incredible patience!
Each has their advantages. Many users run Pi-hole along with a browser based blocker. But, browser based blockers only work at the browser level, not across the entire network.
There are certain ads that are difficult to block with Pi-hole, since they are served from the same domain as the content and Pi-hole is a domain blocker. Browser blockers can also reformat a page on the fly to eliminate the spaces where the ads no longer appear. There is a performance trade-off in exchange.
Yes.
Both tools target a different area.
Pi-hole does suppress DNS answers for unwanted domain names and will do so for any DNS request from your network, regardless whether that has been issued by an OS, browser, app, IoT appliance or any other source. Being centrally managed, it can do so even while your clients are oblivious of Pi-hole's presence.
A browser extension does only filter traffic from your browser and has to be installed on every device in every browser you are using.
But it allows fine-grained control of filtering below domain level, e.g. blocking certain images or scripts. Trying to filter such content with Pi-hole would almost certainly result in overblocking, precluding you from wanted as well as unwanted content.
Again, thank you very much, you've been really patient and helpful
This topic was automatically closed 21 days after the last reply. New replies are no longer allowed.