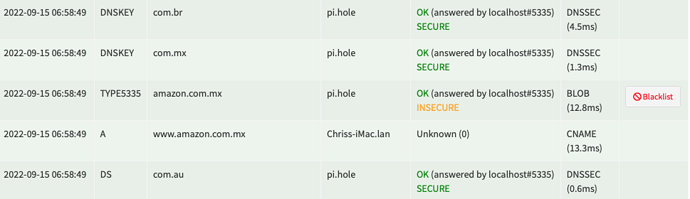
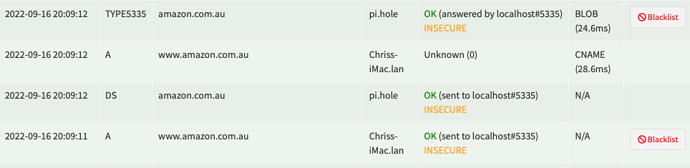
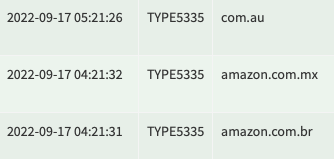
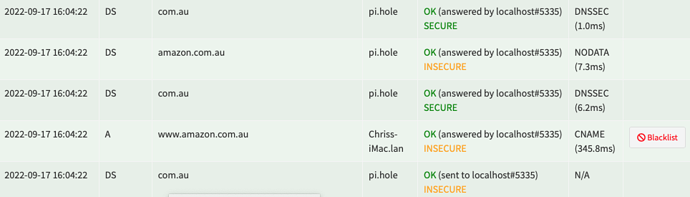
Related log entries for the 1st image, which resulted in the TYPE5335 and BLOB, caused by logging in to Amazon UK and it querying a flurry of amazon-related TLDs, one of which was www.amazon.com.mx
Sep 15 06:58:48 dnsmasq[636]: query[A] www.amazon.com.mx from 192.168.1.121
Sep 15 06:58:48 dnsmasq[636]: forwarded www.amazon.com.mx to 127.0.0.1#5335
Sep 15 06:58:49 dnsmasq[636]: dnssec-query[DS] mx to 127.0.0.1#5335
Sep 15 06:58:49 dnsmasq[636]: reply mx is DS keytag 61885, algo 8, digest 2
Sep 15 06:58:49 dnsmasq[636]: dnssec-query[DS] com.mx to 127.0.0.1#5335
Sep 15 06:58:49 dnsmasq[636]: dnssec-query[DNSKEY] mx to 127.0.0.1#5335
Sep 15 06:58:49 dnsmasq[636]: reply mx is DNSKEY keytag 61885, algo 8
Sep 15 06:58:49 dnsmasq[636]: reply mx is DNSKEY keytag 19441, algo 8
Sep 15 06:58:49 dnsmasq[636]: reply com.mx is DS keytag 61885, algo 8, digest 2
Sep 15 06:58:49 dnsmasq[636]: dnssec-query[DS] amazon.com.mx to 127.0.0.1#5335
Sep 15 06:58:49 dnsmasq[636]: query[A] www.amazon.com.mx from 192.168.1.121
Sep 15 06:58:49 dnsmasq[636]: dnssec-retry[DS] amazon.com.mx to 127.0.0.1#5335
Sep 15 06:58:49 dnsmasq[636]: dnssec-query[DNSKEY] com.mx to 127.0.0.1#5335
Sep 15 06:58:49 dnsmasq[636]: reply com.mx is DNSKEY keytag 61885, algo 8
Sep 15 06:58:49 dnsmasq[636]: reply com.mx is DNSKEY keytag 19441, algo 8
Sep 15 06:58:49 dnsmasq[636]: reply amazon.com.mx is no DS
Sep 15 06:58:49 dnsmasq[636]: reply www.amazon.com.mx is <CNAME>
Sep 15 06:58:49 dnsmasq[636]: reply tp.4e37fb303-frontier.amazon.com.mx is <CNAME>
Sep 15 06:58:49 dnsmasq[636]: reply www.amazon.com.mx.edgekey.net is <CNAME>
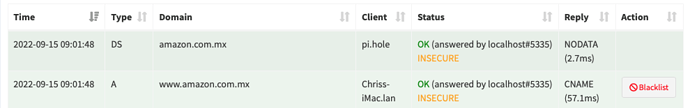
Related log entries for the 2nd image, which was me doing a dig A on the the same domain, and it worked okay
Sep 15 09:01:48 dnsmasq[636]: query[A] www.amazon.com.mx from 192.168.1.121
Sep 15 09:01:48 dnsmasq[636]: forwarded www.amazon.com.mx to 127.0.0.1#5335
Sep 15 09:01:48 dnsmasq[636]: dnssec-query[DS] amazon.com.mx to 127.0.0.1#5335
Sep 15 09:01:48 dnsmasq[636]: reply amazon.com.mx is no DS
Sep 15 09:01:48 dnsmasq[636]: reply www.amazon.com.mx is <CNAME>
Sep 15 09:01:48 dnsmasq[636]: reply tp.4e37fb303-frontier.amazon.com.mx is <CNAME>
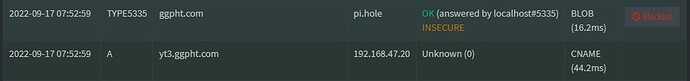
Related log entries for the 3rd image, which was loaded when I visited codepen.io, and saw another entry for TYPE5335 and the BLOB
Sep 16 00:25:23 dnsmasq[2899]: query[A] static.codepen.io from 192.168.1.121
Sep 16 00:25:23 dnsmasq[2899]: forwarded static.codepen.io to 127.0.0.1#5335
Sep 16 00:25:23 dnsmasq[2899]: dnssec-query[DS] io to 127.0.0.1#5335
Sep 16 00:25:23 dnsmasq[2899]: reply io is DS keytag 57355, algo 8, digest 2
Sep 16 00:25:23 dnsmasq[2899]: dnssec-query[DS] codepen.io to 127.0.0.1#5335
Sep 16 00:25:23 dnsmasq[2899]: query[A] codepen.io from 192.168.1.121
Sep 16 00:25:23 dnsmasq[2899]: forwarded codepen.io to 127.0.0.1#5335
Sep 16 00:25:23 dnsmasq[2899]: reply digitalocean1.mktoweb.com is blocked during CNAME inspection
Sep 16 00:25:24 dnsmasq[2899]: query[A] static.codepen.io from 192.168.1.121
Sep 16 00:25:24 dnsmasq[2899]: dnssec-retry[DS] codepen.io to 127.0.0.1#5335
Sep 16 00:25:24 dnsmasq[2899]: dnssec-query[DNSKEY] io to 127.0.0.1#5335
Sep 16 00:25:24 dnsmasq[2899]: reply io is DNSKEY keytag 49206, algo 8
Sep 16 00:25:24 dnsmasq[2899]: reply io is DNSKEY keytag 13608, algo 8
Sep 16 00:25:24 dnsmasq[2899]: reply io is DNSKEY keytag 57355, algo 8
Sep 16 00:25:24 dnsmasq[2899]: reply codepen.io is no DS
Sep 16 00:25:24 dnsmasq[2899]: reply codepen.io is 104.16.176.44
Sep 16 00:25:24 dnsmasq[2899]: reply codepen.io is 104.17.14.48
Sep 16 00:25:24 dnsmasq[2899]: reply static.codepen.io is 104.17.14.48
Sep 16 00:25:24 dnsmasq[2899]: reply static.codepen.io is 104.16.176.44
Note that in all cases I was not aware of anything being wrong, no broken sites or anything, it was only the type OTHER on the dashboard that alerted me to look into it and discover the weird TYPE5335 entry.
I've now temporarily enabled Unbound logging verbosity level 3 to a dedicated log file in case it happens a third time.