That is a valid reasoning, other than it resolves. Is it good practice - no. And I am with you it for sure something of contention.. In a domain its is is valid.
The problem is it does resolve..
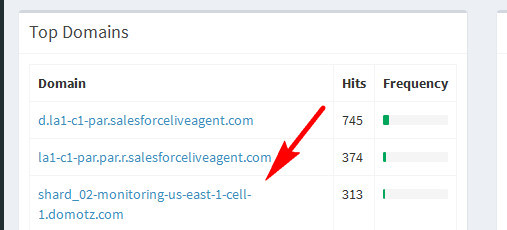
user@ubuntu:~$ dig shard_02-monitoring-us-east-1-cell-1.domotz.com
; <<>> DiG 9.9.5-3ubuntu0.10-Ubuntu <<>> shard_02-monitoring-us-east-1-cell-1.domotz.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 474
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;shard_02-monitoring-us-east-1-cell-1.domotz.com. IN A
;; ANSWER SECTION:
shard_02-monitoring-us-east-1-cell-1.domotz.com. 401 IN A 52.202.223.108
;; Query time: 12 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Fri Dec 23 14:26:07 CST 2016
;; MSG SIZE rcvd: 81
I can reach out to them to remove the _, but since these sorts of fqdn do resolve and work on the public internet - pihole shouldn't reject putting them in to the system not to show them, etc.
https://www.ietf.org/rfc/rfc2181.txt
The DNS itself places only one restriction on the particular labels that can be used to identify resource records. That one restriction relates to the length of the label and the full name. [...] Implementations of the DNS protocols must not place any restrictions on the labels that can be used. In particular, DNS servers must not refuse to serve a zone because it contains labels that might not be acceptable to some DNS client programs.
Now I am with you and do believe rfc https://www.ietf.org/rfc/rfc1034.txt
Puts this limit on host names that are part of a fqdn.
The labels must follow the rules for ARPANET host names. They must
start with a letter, end with a letter or digit, and have as interior
characters only letters, digits, and hyphen. There are also some
restrictions on the length.
So I will reach out to them what looks to be a host in the fqdn having a _
But _ are used in domain names all the time. So to me their validation needs to be loosened.. Since clearly the fqdn is resolving and being listed as one of the top queries, I should be able to not list it.. Be it the owner is following rfc's or not - it clearly resolves, and is listed with pihole as top