me:
sudo cat -n /var/www/html/pihole/index.php | head -n 170 | tail -n 25
146 );$queryAds[0])");
You can try move/backup the current databases to your home folder ~ and start fresh :
sudo service pihole-FTL stop
sudo mv /etc/pihole/{gravity.db,pihole-FTL.db} ~
sudo service pihole-FTL start
pihole -g -r
Ok, done with default adlist of Pi-Hole.
I don't have that file "/etc/pihole/gravity_temp.db"
Error again:
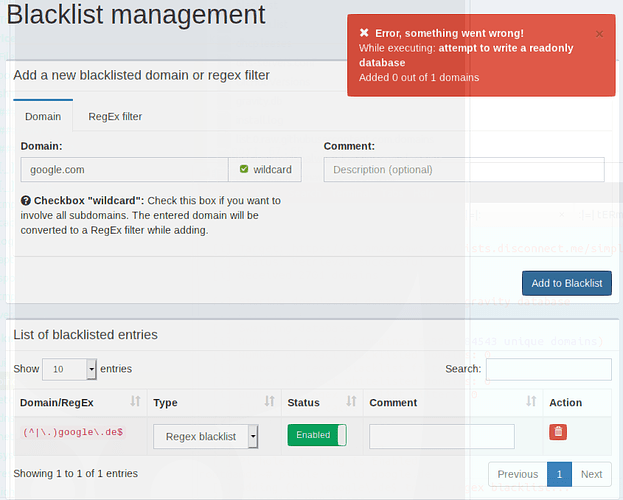
2020-05-29 16:25:35: (mod_fastcgi.c.421) FastCGI-stderr: PHP Warning: SQLite3Stmt::execute(): Unable to execute statement: attempt to write a readonly database in /var/www/html/admin/scripts/pi-hole/php/groups.php on line 507
As you can see:
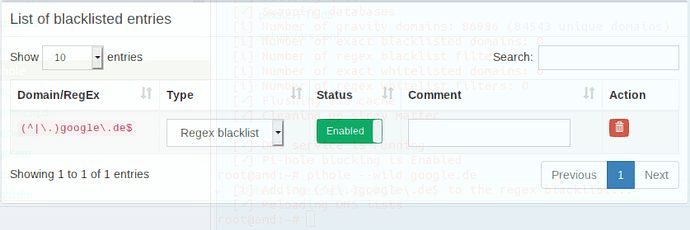
via Terminal:pihole --wild google.de
I dont have that file either:
pi@ph5:~ $ stat /etc/pihole/gravity_temp.db
stat: cannot stat '/etc/pihole/gravity_temp.db': No such file or directory
What hardware is this running on and what distro did you install ?
over Pi-Hole admin-panel in my webbrowser:
Ubuntu 19.04 is running.
Since I've been using Pi-Hole V5 it's been causing trouble with the database.
If this problem cannot be solved then
With Pi-Hole V4 this problem did not exist.
If its your desktop PC, I wouldn't know what is installed/altered.
EDIT: last one ?
mount | grep '/ \|/etc'
yes.
By the way.
See here:
I did a test:sudo service pihole-FTL stop
sudo sqlite3 /etc/pihole/gravity.db "delete from gravity where domain like '%.google.de';"
sudo service pihole-FTL start
Look here:
It's not removed via command above.
sqlite3 does not work to delete google.de from Pi-Hole database.
sqlite3 -version
3.27.2 2019-02-25 16:06:06
bd49a8271d650fa89e446b42e513b595a717b9212c91dd384aab871fc1d0alt1
sqlite3 /etc/pihole/gravity.db
SQLite version 3.27.2 2019-02-25 16:06:06
Enter ".help" for usage hints.
sqlite> .tables
adlist domainlist_by_group vw_gravity
@ all,
I have the solution.
It was these two entries:
PrivateTmp=true ProtectSystem=full
of
/lib/systemd/system/lighttpd.service
I removed these lines and now my Pi-Hole V5 is working 100%
yes
"S O L U T I O N"
1 Like
Glad for you.
This is not intended to remove entries from the blacklist but from the blocklist (gravity). Black - and whitelist are stored in another table (domainlist)
Nice catch!
hostnamectl | tail -3
dpkg -S /lib/systemd/system/lighttpd.service
apt policy lighttpd
@ deHakkelaar
hostnamectl | tail -3
Operating System: Ubuntu 19.04
dpkg -S /lib/systemd/system/lighttpd.service
lighttpd: /lib/systemd/system/lighttpd.service
apt policy lighttpd
lighttpd:
my working lighttpd.service: cat /lib/systemd/system/lighttpd.service
[Unit] Description=####//"lighttpd" After=network.target
[Service] Type=simple ExecStartPre=/usr/sbin/lighttpd -tt -f /etc/lighttpd/lighttpd.conf ExecStart=/usr/sbin/lighttpd -D -f /etc/lighttpd/lighttpd.conf
####//: SeCUr!Ty InaccessiblePaths=/boot ProtectHome=true ProtectKernelTunables=true ProtectKernelModules=true PrivateDevices=true MemoryDenyWriteExecute=true RestrictRealtime=true
[Install] WantedBy=multi-user.target
These parameters block
PrivateTmp=true ProtectSystem=full
Lighttpd from writing to the Pi-Hole database via the admin-panel in my webbrowser.
@ msatter, I'm using not a device. (PI eg.)
anon62498003:
apt policy lighttpd
lighttpd:
That sounds as if you didnt install lighttpd from the official repos:
pi@ph5:~ $ apt policy lighttpd
lighttpd:
Installed: 1.4.53-4
Candidate: 1.4.53-4
Version table:
*** 1.4.53-4 500
500 http://raspbian.raspberrypi.org/raspbian buster/main armhf Packages
100 /var/lib/dpkg/status
Notice the path "http://raspbian.raspberrypi.org/raspbian" where the package is located.
@ deHakkelaar
I got it from Synaptic package manager.
I'm using 2x ethernet usb adapter, one for me to visit websites and at ethernet interface 2 is pi-hole running for localhost.
interface 1 is configured with DHCP (dhcpcd) - me, client
Runs great incl. with https active on Lighttpd.
Greetings!
Greetings!
Well probably if you had installed lighttpd from the official Ubuntu repos, you wouldnt have had these issues.
Cheers!
1 Like
So, the TLDR of this is:
I told lighttpd to not access files:
####//: SeCUr!Ty
InaccessiblePaths=/boot
ProtectHome=true
ProtectKernelTunables=true
ProtectKernelModules=true
PrivateDevices=true
MemoryDenyWriteExecute=true
RestrictRealtime=true
It broke Pi-hole when it couldn't access files.
1 Like