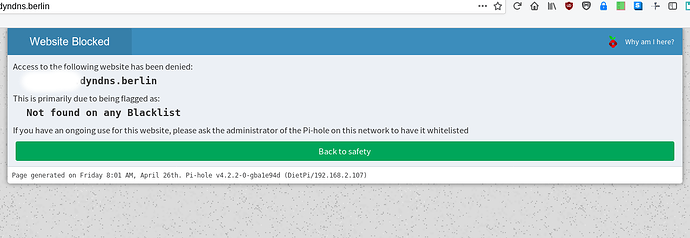
I don't think so.
Normally there should be come the debian default webpage. But since I have installed pihole
and you try to access the default page there come an answer from pihole which denid me the access.
And so I think pihole is also preventing certbot to create the file in .well-known/acme-challenge.
Hopefilly I have drscribed the problem right. Maybe I have to change webroot ?
Micha