I think we have established that Pi-hole is using the configured Upstream DNS Servers, and the problem is not with your Pi-hole install. I will move this topic to the General category and change the title accordingly.
Sounds good, but I mean it's more than just the DNS leak test showing odd behavior. The OpenDNS verification sites all say I'm using OpenDNS. If I block all traffic to OpenDNS, by DNS is completely broken, even though looking at the raw tcpdump it shows DNS going to Quad9....
So damn weird. So weird.
Take Pi-hole out of the picture, block OpenDNS on the router and try to resolve with a client. See if it's the router that is redirecting queries.
Sounds good, I'll give it a shot. So for this I'd be pointing the client to the router for DNS, pointing the router to Cloudflare/Quad9 for DNS (literally anything other than OpenDNS), and then blocking OpenDNS IPs at the router. Does that sound like what you were thinking? Or were you thinking point the clients directly to Cloudflare/Quad9 for DNS? And just use the router to block OpenDNS IPs?
Try any and all of the options.
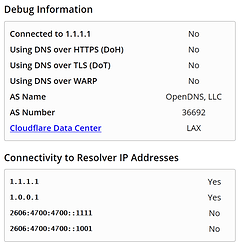
Alrighty @DanSchaper, done with work so this has my full attention now. I chose Cloudflare to test with this as they have a page you can go to to check if you're using them (https://1.1.1.1/help).
TLDR; No idea what the hell is going on, but it still seems like the PiHole is somehow making it appear as though I'm using OpenDNS.....even though I'm not. Do I just reinstall at this point?? Maybe there is some other config file in the pi system that is causing this? Resolv.conf only shows one name server though, itself (192.168.1.100). You'll see further down, but that fact that if I use the PiHole for DNS, block OpenDNS at the router, and all my DNS fails, certainly makes it seem like the pi is forwarding to OpenDNS, even though the logs indicate it's not. TCPDump also indicates it's not forward to OpenDNS. I'd call this a weird cosmetic issue, but the blocking of OpenDNS paired with my DNS failing is super strange.
Dan - any chance you could test this out as well? Not as extensively, but just go to the OpenDNS test pages I've linked, do they tell you you're using OpenDNS?
TEST #1 : Client DNS -> Router , Router DNS -> Cloudflare (1.1.1.1), OpenDNS blocked at router
- Cloudflare test site - Connected to 1.1.1.1 (link to results here)
- OpenDNS test site (welcome.opendns.com) - not using OpenDNS
** So it appears my router is not sending to OpenDNS, it's sending to Cloudflare - DNS Leak Test
Test complete
Servers found = 1
| IP | Hostname | ISP | Country |
|---|---|---|---|
| 108.162.236.22 | None | Cloudflare | Atlanta, United States |
TEST #2 : Client DNS -> Cloudflare (1.1.1.1), OpenDNS blocked at router
- Same results as above
** So it also appears my router / ISP is not intercepting DNS requests and sending to OpenDNS.
==========================================================================
Now to bring the pihole back into the equation.... (I flushed DNS cache on pi, router, and client before doing this next part)
- pihole = 192.168.1.100
- client = 192.168.1.233
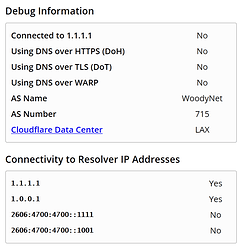
TEST #1 : Client DNS -> PiHole, PiHole -> Cloudflare
- Cloudflare test site - Not connected to 1.1.1.1 (doesn't provide a link to results when not connected like above)
- OpenDNS test site (welcome.opendns.com) - Using OpenDNS
- OpenDNS test block page (internetbadguys.com) - Blocked by OpenDNS
- DNS Leak Test
Test Complete
Servers found = 10
| IP | Hostname | ISP | Country |
|---|---|---|---|
| 146.112.137.64 | r1.compute.atl1.edc.strln.net. | Cisco OpenDNS, LLC | Atlanta, United States |
| 146.112.137.65 | r2.compute.atl1.edc.strln.net. | Cisco OpenDNS, LLC | Atlanta, United States |
| 146.112.137.66 | r3.compute.atl1.edc.strln.net. | Cisco OpenDNS, LLC | Atlanta, United States |
| 146.112.137.67 | r4.compute.atl1.edc.strln.net. | Cisco OpenDNS, LLC | Atlanta, United States |
| 146.112.137.68 | r5.compute.atl1.edc.strln.net. | Cisco OpenDNS, LLC | Atlanta, United States |
| 146.112.137.69 | r6.compute.atl1.edc.strln.net. | Cisco OpenDNS, LLC | Atlanta, United States |
| 146.112.137.70 | r7.compute.atl1.edc.strln.net. | Cisco OpenDNS, LLC | Atlanta, United States |
| 146.112.137.71 | r8.compute.atl1.edc.strln.net. | Cisco OpenDNS, LLC | Atlanta, United States |
| 146.112.137.72 | r9.compute.atl1.edc.strln.net. | Cisco OpenDNS, LLC | Atlanta, United States |
| 146.112.137.73 | r10.compute.atl1.edc.strln.net. | Cisco OpenDNS, LLC | Atlanta, United States |
TEST #2 : Client DNS -> PiHole, PiHole -> Cloudflare, OpenDNS blocked at router
- All DNS requests / tests fail
pihole -d is here: https://tricorder.pi-hole.net/z8p7owqnrc
Some interesting PiHole Logs, grepped for "forwarded|192.168.1.233"
Jul 2 15:53:39 dnsmasq[26377]: query[A] embed.cloudflarestream.com from 192.168.1.233
Jul 2 15:53:39 dnsmasq[26377]: forwarded embed.cloudflarestream.com to 1.0.0.1
Jul 2 15:53:39 dnsmasq[26377]: query[A] www.google-analytics.com from 192.168.1.233
Jul 2 15:53:39 dnsmasq[26377]: query[A] embed.cloudflarestream.com from 192.168.1.233
Jul 2 15:53:39 dnsmasq[26377]: query[AAAA] embed.cloudflarestream.com from 192.168.1.233
Jul 2 15:53:39 dnsmasq[26377]: forwarded embed.cloudflarestream.com to 1.0.0.1
Jul 2 15:53:40 dnsmasq[26377]: query[A] www.googletagmanager.com from 192.168.1.233
Jul 2 15:53:40 dnsmasq[26377]: query[A] b2863a5f-0feb-4026-bd1f-db78608dbd67.is-cf.cloudflareresolve.com from 192.168.1.233
Jul 2 15:53:40 dnsmasq[26377]: forwarded b2863a5f-0feb-4026-bd1f-db78608dbd67.is-cf.cloudflareresolve.com to 1.0.0.1
Jul 2 15:53:41 dnsmasq[26377]: query[A] b2863a5f-0feb-4026-bd1f-db78608dbd67.is-dot.cloudflareresolve.com from 192.168.1.233
Jul 2 15:53:41 dnsmasq[26377]: forwarded b2863a5f-0feb-4026-bd1f-db78608dbd67.is-dot.cloudflareresolve.com to 1.0.0.1
Jul 2 15:53:41 dnsmasq[26377]: query[A] b2863a5f-0feb-4026-bd1f-db78608dbd67.is-doh.cloudflareresolve.com from 192.168.1.233
Jul 2 15:53:41 dnsmasq[26377]: forwarded b2863a5f-0feb-4026-bd1f-db78608dbd67.is-doh.cloudflareresolve.com to 1.0.0.1
Jul 2 15:53:41 dnsmasq[26377]: query[A] ipv6b.cloudflare-dns.com from 192.168.1.233
Jul 2 15:53:41 dnsmasq[26377]: forwarded ipv6b.cloudflare-dns.com to 1.0.0.1
Jul 2 15:53:41 dnsmasq[26377]: query[A] ipv6a.cloudflare-dns.com from 192.168.1.233
Jul 2 15:53:41 dnsmasq[26377]: forwarded ipv6a.cloudflare-dns.com to 1.0.0.1
Jul 2 15:53:41 dnsmasq[26377]: query[A] b2863a5f-0feb-4026-bd1f-db78608dbd67.map.cloudflareresolve.com from 192.168.1.233
Jul 2 15:53:41 dnsmasq[26377]: forwarded b2863a5f-0feb-4026-bd1f-db78608dbd67.map.cloudflareresolve.com to 1.0.0.1
Jul 2 15:53:41 dnsmasq[26377]: query[A] b2863a5f-0feb-4026-bd1f-db78608dbd67.map.cloudflareresolve.com from 192.168.1.233
Jul 2 15:53:41 dnsmasq[26377]: forwarded b2863a5f-0feb-4026-bd1f-db78608dbd67.map.cloudflareresolve.com to 1.0.0.1
Jul 2 15:53:44 dnsmasq[26377]: query[A] dnsleaktest.com from 192.168.1.233
Jul 2 15:53:44 dnsmasq[26377]: forwarded dnsleaktest.com to 1.0.0.1
Jul 2 15:53:44 dnsmasq[26377]: query[A] dnsleaktest.com from 192.168.1.233
Jul 2 15:53:44 dnsmasq[26377]: query[AAAA] dnsleaktest.com from 192.168.1.233
Jul 2 15:53:44 dnsmasq[26377]: forwarded dnsleaktest.com to 1.0.0.1
Jul 2 15:53:44 dnsmasq[26377]: query[A] www.dnsleaktest.com from 192.168.1.233
Jul 2 15:53:44 dnsmasq[26377]: forwarded www.dnsleaktest.com to 1.0.0.1
Jul 2 15:53:44 dnsmasq[26377]: query[A] www.dnsleaktest.com from 192.168.1.233
Jul 2 15:53:44 dnsmasq[26377]: query[AAAA] www.dnsleaktest.com from 192.168.1.233
Jul 2 15:53:44 dnsmasq[26377]: forwarded www.dnsleaktest.com to 1.0.0.1
Jul 2 15:58:35 dnsmasq[26377]: query[A] welcome.opendns.com from 192.168.1.233
Jul 2 15:58:35 dnsmasq[26377]: forwarded welcome.opendns.com to 1.0.0.1
Jul 2 15:58:35 dnsmasq[26377]: query[A] s3-us-west-1.amazonaws.com from 192.168.1.233
Jul 2 15:58:35 dnsmasq[26377]: forwarded s3-us-west-1.amazonaws.com to 1.0.0.1
Jul 2 15:58:35 dnsmasq[26377]: reply welcome.opendns.com is
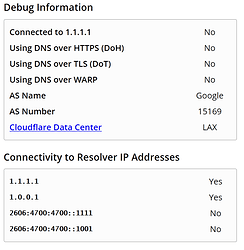
TEST #3 : Client DNS -> PiHole, PiHole -> Google DNS
- Cloudflare test site - Not connected to 1.1.1.1 (this is expected)
- OpenDNS test site (welcome.opendns.com) - Using OpenDNS
- OpenDNS test block page (internetbadguys.com) - Blocked by OpenDNS
More pihole logs, appears to be forwarding to Google DNS.
Jul 2 16:02:42 dnsmasq[29117]: query[A] www.internetbadguys.com from 192.168.1.233
Jul 2 16:02:42 dnsmasq[29117]: forwarded www.internetbadguys.com to 8.8.4.4
Jul 2 16:02:42 dnsmasq[29117]: query[A] www.internetbadguys.com from 192.168.1.233
Jul 2 16:02:42 dnsmasq[29117]: forwarded www.internetbadguys.com to 8.8.4.4
Jul 2 16:02:42 dnsmasq[29117]: query[A] www.internetbadguys.com from 192.168.1.233
Jul 2 16:02:42 dnsmasq[29117]: forwarded www.internetbadguys.com to 8.8.4.4
Jul 2 16:02:42 dnsmasq[29117]: query[AAAA] www.internetbadguys.com from 192.168.1.233
Jul 2 16:02:42 dnsmasq[29117]: forwarded www.internetbadguys.com to 8.8.4.4
Jul 2 16:02:42 dnsmasq[29117]: query[A] phish.opendns.com from 192.168.1.233
Jul 2 16:02:42 dnsmasq[29117]: forwarded phish.opendns.com to 8.8.4.4
Jul 2 16:02:42 dnsmasq[29117]: query[A] phish.opendns.com from 192.168.1.233
Jul 2 16:02:42 dnsmasq[29117]: forwarded phish.opendns.com to 8.8.4.4
Jul 2 16:02:42 dnsmasq[29117]: query[A] phish.proxy.umbrella.opendns.com from 192.168.1.233
Jul 2 16:02:42 dnsmasq[29117]: forwarded phish.proxy.umbrella.opendns.com to 8.8.4.4
Jul 2 16:02:42 dnsmasq[29117]: query[AAAA] phish.proxy.umbrella.opendns.com from 192.168.1.233
Jul 2 16:02:42 dnsmasq[29117]: forwarded phish.proxy.umbrella.opendns.com to 8.8.4.4
Jul 2 16:02:42 dnsmasq[29117]: query[A] www.internetbadguys.com from 192.168.1.233
Jul 2 16:02:42 dnsmasq[29117]: forwarded www.internetbadguys.com to 8.8.4.4
Jul 2 16:02:42 dnsmasq[29117]: query[A] www.internetbadguys.com from 192.168.1.233
Jul 2 16:02:42 dnsmasq[29117]: forwarded www.internetbadguys.com to 8.8.4.4
Jul 2 16:02:42 dnsmasq[29117]: query[A] www.internetbadguys.com.x.b634beb509aed04a4f083cc06aad213c74ac.d0452022.id.opendns.com from 192.168.1.233
Jul 2 16:02:42 dnsmasq[29117]: forwarded www.internetbadguys.com.x.b634beb509aed04a4f083cc06aad213c74ac.d0452022.id.opendns.com to 8.8.4.4
Jul 2 16:02:42 dnsmasq[29117]: query[AAAA] www.internetbadguys.com from 192.168.1.233
Jul 2 16:02:42 dnsmasq[29117]: forwarded www.internetbadguys.com to 8.8.4.4
Jul 2 16:02:42 dnsmasq[29117]: query[A] www.internetbadguys.com.x.b634beb509aed04a4f083cc06aad213c74ac.d0452022.id.opendns.com from 192.168.1.233
Jul 2 16:02:42 dnsmasq[29117]: query[AAAA] www.internetbadguys.com.x.b634beb509aed04a4f083cc06aad213c74ac.d0452022.id.opendns.com from 192.168.1.233
Jul 2 16:02:42 dnsmasq[29117]: forwarded www.internetbadguys.com.x.b634beb509aed04a4f083cc06aad213c74ac.d0452022.id.opendns.com to 8.8.4.4
What about https://welcome.opendns.com and www.internetbadguys.com? With something other than OpenDNS as your upstream. Those are the two sites that mainly indicate I'm using OpenDNS...even though the pi is set to literally any other provider except them. The 1.1.1.1/help was useful to see if I was using Cloudflare, but not so much in determining the OpenDNS stuff.
This is certainly beyond the level of support I'd expect for a free product in an open forum, but I seriously appreciate your help. This is just so weird.
Oops for everything but OpenDNS, orange check for OpenDNS. (Though I did have to CTRL-F5 a few times and flush the cache of DNS and browser between upstream changes.)
What browser are you using? Is DoH or DoT enabled, with or without your knowledge?
Huh....now I'm even more confused I think. So you were using an upstream provide other than OpenDNS, but you still got the orange check on the OpenDNS test site? What in the hell.
It's the blocking at the router that really throws me for a loop. Pihole is set to use Cloudflare for DNS, me blocking the OpenDNS IP's should have zero impact on anything. But if clients are using pihole for DNS with the OpenDNS blocking on the router, all DNS fails. I suppose I could pull the firewall logs from the router, those would be interesting to take a look at. Also want a tcpdump from the router port the pi is on, have to do a little trickery to get that going though.
I'm torn between going down that path, or just doing a full uninstall of pihole and resinstalling to see if that changes anything. If it doesn't, I'm a few headaches away from reimaging the whole pi (which would suck a lot, have quite a few things running on the little guy).
Browser has been a mix of IE, Edge, Chrome, Firefox. I know firefox has some built in DNS security so I've tried avoiding that one.
Just to check Firefox, I confirmed the DoH setting was off. With it off, 1.1.1.1/help says I'm not using them or DOH. OpenDNS says I'm using them (still pointing to the pihole, which is set to Cloudflare).
If I enable DoH in firefox, 1.1.1.1/help says I am using them and DoH...but OpenDNS STILL SAYS I'M USING THEM. What the hell.
Hence why I've avoided using firefox for the testing 
Checking firewall logs now.....we'll see whats in there. The only problem is it takes all of DNS down when I block the OpenDNS IP's at the router 
No, red check for any non-OpenDNS, orange check for OpenDNS and only OpenDNS.
IGNORE THAT UPDATE, HAD THE FIREWALL RULE WRONG. Updating now...one sec.
So current state is all devices on network are point to the pihole and nothing else for DNS. All laptops, PC's, hell even the router (on the off chance it gets a DNS request, which it shouldn't) is pointing to the pihole. See below for firewall logs from the router. Tons of blocked traffic from the pihole (192.168.1.100) to OpenDNs (208.67.222.222). Pihole upstream is currently set as Cloudflare.
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=70 TOS=0x00 PREC=0x00 TTL=63 ID=58779 DF PROTO=UDP SPT=42967 DPT=53 LEN=50
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=70 TOS=0x00 PREC=0x00 TTL=63 ID=39635 DF PROTO=UDP SPT=42967 DPT=53 LEN=50
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=63 TOS=0x00 PREC=0x00 TTL=63 ID=58782 DF PROTO=UDP SPT=53886 DPT=53 LEN=43
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=63 TOS=0x00 PREC=0x00 TTL=63 ID=39636 DF PROTO=UDP SPT=53886 DPT=53 LEN=43
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=68 TOS=0x00 PREC=0x00 TTL=63 ID=58783 DF PROTO=UDP SPT=47009 DPT=53 LEN=48
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=68 TOS=0x00 PREC=0x00 TTL=63 ID=39637 DF PROTO=UDP SPT=47009 DPT=53 LEN=48
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=64 TOS=0x00 PREC=0x00 TTL=63 ID=58784 DF PROTO=UDP SPT=47009 DPT=53 LEN=44
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=64 TOS=0x00 PREC=0x00 TTL=63 ID=39638 DF PROTO=UDP SPT=47009 DPT=53 LEN=44
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=69 TOS=0x00 PREC=0x00 TTL=63 ID=58785 DF PROTO=UDP SPT=58068 DPT=53 LEN=49
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=69 TOS=0x00 PREC=0x00 TTL=63 ID=39639 DF PROTO=UDP SPT=58068 DPT=53 LEN=49
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=61 TOS=0x00 PREC=0x00 TTL=63 ID=58786 DF PROTO=UDP SPT=56918 DPT=53 LEN=41
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=61 TOS=0x00 PREC=0x00 TTL=63 ID=39646 DF PROTO=UDP SPT=56918 DPT=53 LEN=41
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=74 TOS=0x00 PREC=0x00 TTL=63 ID=58788 DF PROTO=UDP SPT=44912 DPT=53 LEN=54
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=74 TOS=0x00 PREC=0x00 TTL=63 ID=39647 DF PROTO=UDP SPT=44912 DPT=53 LEN=54
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=72 TOS=0x00 PREC=0x00 TTL=63 ID=58789 DF PROTO=UDP SPT=47009 DPT=53 LEN=52
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=72 TOS=0x00 PREC=0x00 TTL=63 ID=39652 DF PROTO=UDP SPT=47009 DPT=53 LEN=52
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=65 TOS=0x00 PREC=0x00 TTL=63 ID=58803 DF PROTO=UDP SPT=52877 DPT=53 LEN=45
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=65 TOS=0x00 PREC=0x00 TTL=63 ID=39662 DF PROTO=UDP SPT=52877 DPT=53 LEN=45
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=88 TOS=0x00 PREC=0x00 TTL=63 ID=58804 DF PROTO=UDP SPT=47009 DPT=53 LEN=68
Jul 2 17:45:36 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=88 TOS=0x00 PREC=0x00 TTL=63 ID=39663 DF PROTO=UDP SPT=47009 DPT=53 LEN=68
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=85 TOS=0x00 PREC=0x00 TTL=63 ID=58809 DF PROTO=UDP SPT=47009 DPT=53 LEN=65
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=85 TOS=0x00 PREC=0x00 TTL=63 ID=39667 DF PROTO=UDP SPT=47009 DPT=53 LEN=65
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=76 TOS=0x00 PREC=0x00 TTL=63 ID=58811 DF PROTO=UDP SPT=47009 DPT=53 LEN=56
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=76 TOS=0x00 PREC=0x00 TTL=63 ID=39676 DF PROTO=UDP SPT=47009 DPT=53 LEN=56
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=67 TOS=0x00 PREC=0x00 TTL=63 ID=58813 DF PROTO=UDP SPT=16222 DPT=53 LEN=47
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=67 TOS=0x00 PREC=0x00 TTL=63 ID=39679 DF PROTO=UDP SPT=16222 DPT=53 LEN=47
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=74 TOS=0x00 PREC=0x00 TTL=63 ID=58829 DF PROTO=UDP SPT=10954 DPT=53 LEN=54
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=74 TOS=0x00 PREC=0x00 TTL=63 ID=39686 DF PROTO=UDP SPT=10954 DPT=53 LEN=54
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=65 TOS=0x00 PREC=0x00 TTL=63 ID=58830 DF PROTO=UDP SPT=47526 DPT=53 LEN=45
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=65 TOS=0x00 PREC=0x00 TTL=63 ID=39687 DF PROTO=UDP SPT=47526 DPT=53 LEN=45
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=70 TOS=0x00 PREC=0x00 TTL=63 ID=58831 DF PROTO=UDP SPT=42967 DPT=53 LEN=50
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=70 TOS=0x00 PREC=0x00 TTL=63 ID=39688 DF PROTO=UDP SPT=42967 DPT=53 LEN=50
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=63 TOS=0x00 PREC=0x00 TTL=63 ID=58834 DF PROTO=UDP SPT=53886 DPT=53 LEN=43
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=63 TOS=0x00 PREC=0x00 TTL=63 ID=39689 DF PROTO=UDP SPT=53886 DPT=53 LEN=43
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=68 TOS=0x00 PREC=0x00 TTL=63 ID=58835 DF PROTO=UDP SPT=47009 DPT=53 LEN=48
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=68 TOS=0x00 PREC=0x00 TTL=63 ID=39690 DF PROTO=UDP SPT=47009 DPT=53 LEN=48
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=64 TOS=0x00 PREC=0x00 TTL=63 ID=58836 DF PROTO=UDP SPT=47009 DPT=53 LEN=44
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=64 TOS=0x00 PREC=0x00 TTL=63 ID=39691 DF PROTO=UDP SPT=47009 DPT=53 LEN=44
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=69 TOS=0x00 PREC=0x00 TTL=63 ID=58837 DF PROTO=UDP SPT=58068 DPT=53 LEN=49
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=69 TOS=0x00 PREC=0x00 TTL=63 ID=39692 DF PROTO=UDP SPT=58068 DPT=53 LEN=49
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=80 TOS=0x00 PREC=0x00 TTL=63 ID=58838 DF PROTO=UDP SPT=1612 DPT=53 LEN=60
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=80 TOS=0x00 PREC=0x00 TTL=63 ID=39693 DF PROTO=UDP SPT=1612 DPT=53 LEN=60
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=66 TOS=0x00 PREC=0x00 TTL=63 ID=58846 DF PROTO=UDP SPT=38335 DPT=53 LEN=46
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=66 TOS=0x00 PREC=0x00 TTL=63 ID=39702 DF PROTO=UDP SPT=38335 DPT=53 LEN=46
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=72 TOS=0x00 PREC=0x00 TTL=63 ID=58862 DF PROTO=UDP SPT=47009 DPT=53 LEN=52
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=72 TOS=0x00 PREC=0x00 TTL=63 ID=39716 DF PROTO=UDP SPT=47009 DPT=53 LEN=52
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=68 TOS=0x00 PREC=0x00 TTL=63 ID=58869 DF PROTO=UDP SPT=27302 DPT=53 LEN=48
Jul 2 17:45:37 kernel: DROP IN=br0 OUT=vlan2 SRC=192.168.1.100 DST=208.67.222.222 LEN=68 TOS=0x00 PREC=0x00 TTL=63 ID=39724 DF PROTO=UDP SPT=27302 DPT=53 LEN=48
I don't know what to tell you. Pi-hole is definitively NOT using OpenDNS. I see you have vLANs configured, what are you using to route the vLAN packets among the collision domains? How is the bridge configured to handle vLAN traffic isolation?
Are you using IPTables on the Pi-hole device? Do you have mangle chains or NAT going on?
No IPTables or NAT on the pihole. Vlan2 is for the connection to the cable modem. Not the comcast modem/ router monstrosity, just a little Arris cable modem I'm using, it has no routing capabilities it's just in passthrough mode. Router is an Asus rt-ac68u running Merlin. The vlans are automatically created by the router.
Network setup is this:
Cable modem----Router WAN Port (eth0, vlan2)-----pi directly connected to router eth1 (vlan1). All traffic coming in from vlan one goes out eth0 (vlan2).
I don't know what to say either. The pihole is not set to use OpenDNS, but the router is seeing a ton of UPD 53 traffic come directly from the pihole destined for OpenDNS servers. My only guess is there's some random line of code somewhere on the pi that is forcing DNS to go to the OpenDNS IP's. That's the only the that explains the router seeing traffic come from the pi destined for OpenDNS IP's....right?
We've confirmed the router isn't interfering here, when clients point to the router Cloudflare DNS works fine.
I don't know what else to do here besides blow the pi away and reimage it. There's got to be something in there messing with the DNS traffic, or else why would we see DNS traffic coming from the PI going to OpenDNS in the firewall logs?
Agreed on this, it's got to be something else on the pi that's causing this mix up. All pihole configs look correct. It's got to be another config hiding somewhere. That's the only way the router would be seeing DNS traffic to OpenDNS from the pi IP address.
Right...? The TCPDump is still confusing, that definitely showed DNS going to Cloudflare from the pi. Didn't show any DNS going to OpenDNS.
Check iptables to be sure.
How are you doing that? What are you using to route traffic across the two networks?
Sniff the Pi-hole device for all 53 traffic (make sure you get both TCP and UDP). Sniff the router on both vLAN interfaces to see 53 TCP/UDP moving from vLAN to vLAN.