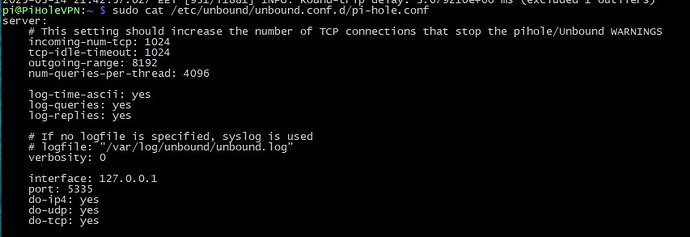
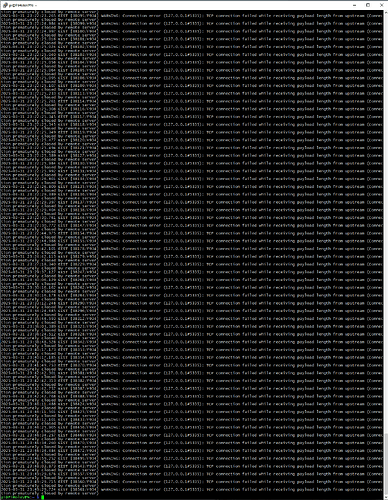
Pi-hole v5 didn't log Connection prematurely closed by remote server messages, they have been added with v6, see Periodic CONNECTION_ERRORs in Diagnostics - Failed to send TCP (read_write) to 127.0.0.1#5335 - #14 by DL6ER.
That's not the key statement.
TCP retries are perfectly normal.
The DNS protocol encourages clients to use UDP by default, but if a DNS reply does exceed UDP packet length, a client may resend the DNS request via TCP, which supports multi packet transport.
The key statement is this:
The summary is that this is not an Unbound issue. The "issue" is extra harmless logging on pihole v6.
With regards to the message itself, I have a differentiated view:
No, Connection prematurely closed by remote server definitely is caused by unbound throwing away TCP connections.
The linked GitHub issue has identified two potential causes for this:
a. unbound exceeds its timeout threshold when walking the recursion chain, which is more likely to happen for misconfigured domains, and unbound then terminates the connection.
b. a new TCP request from a client exceeds unbound's TCP connection pool, so unbound terminates a TCP connection.
The former could only be addressed by adjusting configuration on the authoritative DNS servers by the maintainers of the misconfigured domain.
Increasing unbound's incoming-num-tcp over its default of 10 would affect the latter. Note that unbound maintainers considered already a value of 100 as excessive (requiring more memory), and increasing this value beyond 150 (Pi-hole's internal limit on concurrent connections) would not be likely to result in further improvements.
Depending on the cause for termination of TCP connection, it could still be beneficial to adjust unbound, but even then, the message could still be triggered under heavy load or when querying a misconfigured domain.
While the client whose DNS query prompted that message will have to repeat its query, this doesn't impact DNS resolution in general - that is to say it wouldn't be unusual to observe the message occasionally.