I have a chromecast, DHCP provides the DNS server (pihole), but the chromecast simply ignores the DHCP provided DNS server.
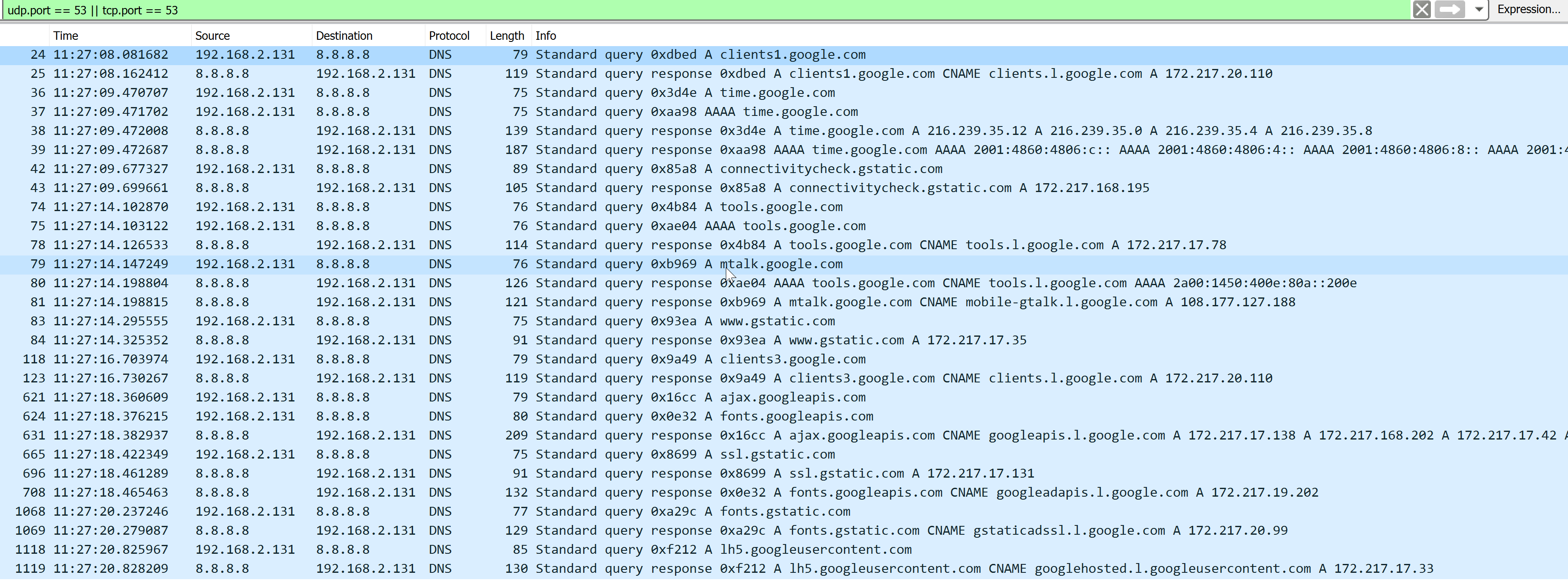
This is what happens if I simply power on the chromecast, up to the moment the first picture appears on screen (chromecast IP 192.168.2.131):
As you can see, the chromecast simply ignores the DHCP provided DNS server and uses the hardcoded 8.8.8.8 (google DNS server).
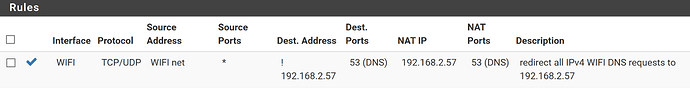
Because I have a NAT rule on the firewall, everything going to 8.8.8.8 is redirected to the pihole. The rule applies to all devices on the WIFI adapter and the destination is NOT the pihole (192.168.2.57). Some other devices are actually using the DHCP provided DNS settings, so redirection is NOT required.
Warning !!! In this example, the pihole is on a different physical network (wired - ethernet), this rule will NOT work if you are using pihole on WIFI. The pihole will NOT be able to resolve DNS requests.
As a result, the firewall intercepts all DNS requests from the chromecast and redirects them to the pihole. In the pihole log (/var/log/pihole.log) the following entries are logged, proving the DNS requests are redirected:
May 5 11:27:08 dnsmasq[8769]: query[A] clients1.google.com from 192.168.2.131
May 5 11:27:08 dnsmasq[8769]: forwarded clients1.google.com to 127.10.10.2
May 5 11:27:08 dnsmasq[8769]: reply clients1.google.com is <CNAME>
May 5 11:27:08 dnsmasq[8769]: reply clients.l.google.com is 172.217.20.110
May 5 11:27:09 dnsmasq[8769]: query[A] time.google.com from 192.168.2.131
May 5 11:27:09 dnsmasq[8769]: cached time.google.com is 216.239.35.12
May 5 11:27:09 dnsmasq[8769]: cached time.google.com is 216.239.35.0
May 5 11:27:09 dnsmasq[8769]: cached time.google.com is 216.239.35.4
May 5 11:27:09 dnsmasq[8769]: cached time.google.com is 216.239.35.8
May 5 11:27:09 dnsmasq[8769]: query[AAAA] time.google.com from 192.168.2.131
May 5 11:27:09 dnsmasq[8769]: cached time.google.com is 2001:4860:4806:c::
May 5 11:27:09 dnsmasq[8769]: cached time.google.com is 2001:4860:4806:4::
May 5 11:27:09 dnsmasq[8769]: cached time.google.com is 2001:4860:4806:8::
May 5 11:27:09 dnsmasq[8769]: cached time.google.com is 2001:4860:4806::
May 5 11:27:09 dnsmasq[8769]: query[A] connectivitycheck.gstatic.com from 192.168.2.131
May 5 11:27:09 dnsmasq[8769]: forwarded connectivitycheck.gstatic.com to 127.10.10.2
May 5 11:27:09 dnsmasq[8769]: reply connectivitycheck.gstatic.com is 172.217.168.195
May 5 11:27:14 dnsmasq[8769]: query[A] tools.google.com from 192.168.2.131
May 5 11:27:14 dnsmasq[8769]: cached tools.google.com is <CNAME>
May 5 11:27:14 dnsmasq[8769]: forwarded tools.google.com to 127.10.10.2
May 5 11:27:14 dnsmasq[8769]: query[AAAA] tools.google.com from 192.168.2.131
May 5 11:27:14 dnsmasq[8769]: forwarded tools.google.com to 127.10.10.2
May 5 11:27:14 dnsmasq[8769]: reply tools.google.com is <CNAME>
May 5 11:27:14 dnsmasq[8769]: reply tools.l.google.com is 172.217.17.78
May 5 11:27:14 dnsmasq[8769]: query[A] mtalk.google.com from 192.168.2.131
May 5 11:27:14 dnsmasq[8769]: cached mtalk.google.com is <CNAME>
May 5 11:27:14 dnsmasq[8769]: forwarded mtalk.google.com to 127.10.10.2
May 5 11:27:14 dnsmasq[8769]: reply tools.google.com is <CNAME>
May 5 11:27:14 dnsmasq[8769]: reply tools.l.google.com is 2a00:1450:400e:80a::200e
May 5 11:27:14 dnsmasq[8769]: reply mtalk.google.com is <CNAME>
May 5 11:27:14 dnsmasq[8769]: reply mobile-gtalk.l.google.com is 108.177.127.188
May 5 11:27:14 dnsmasq[8769]: query[A] www.gstatic.com from 192.168.2.131
May 5 11:27:14 dnsmasq[8769]: forwarded www.gstatic.com to 127.10.10.2
May 5 11:27:14 dnsmasq[8769]: reply www.gstatic.com is 172.217.17.35
May 5 11:27:16 dnsmasq[8769]: query[A] clients3.google.com from 192.168.2.131
May 5 11:27:16 dnsmasq[8769]: forwarded clients3.google.com to 127.10.10.2
May 5 11:27:16 dnsmasq[8769]: reply clients3.google.com is <CNAME>
May 5 11:27:16 dnsmasq[8769]: reply clients.l.google.com is 172.217.20.110
May 5 11:27:18 dnsmasq[8769]: query[A] ajax.googleapis.com from 192.168.2.131
May 5 11:27:18 dnsmasq[8769]: forwarded ajax.googleapis.com to 127.10.10.2
May 5 11:27:18 dnsmasq[8769]: query[A] fonts.googleapis.com from 192.168.2.131
May 5 11:27:18 dnsmasq[8769]: forwarded fonts.googleapis.com to 127.10.10.2
May 5 11:27:18 dnsmasq[8769]: reply ajax.googleapis.com is <CNAME>
May 5 11:27:18 dnsmasq[8769]: reply googleapis.l.google.com is 172.217.17.138
May 5 11:27:18 dnsmasq[8769]: reply googleapis.l.google.com is 172.217.168.202
May 5 11:27:18 dnsmasq[8769]: reply googleapis.l.google.com is 172.217.17.42
May 5 11:27:18 dnsmasq[8769]: reply googleapis.l.google.com is 172.217.168.234
May 5 11:27:18 dnsmasq[8769]: reply googleapis.l.google.com is 172.217.20.106
May 5 11:27:18 dnsmasq[8769]: reply googleapis.l.google.com is 216.58.211.106
May 5 11:27:18 dnsmasq[8769]: query[A] ssl.gstatic.com from 192.168.2.131
May 5 11:27:18 dnsmasq[8769]: forwarded ssl.gstatic.com to 127.10.10.2
May 5 11:27:18 dnsmasq[8769]: reply ssl.gstatic.com is 172.217.17.131
May 5 11:27:18 dnsmasq[8769]: reply fonts.googleapis.com is <CNAME>
May 5 11:27:18 dnsmasq[8769]: reply googleadapis.l.google.com is 172.217.19.202
May 5 11:27:20 dnsmasq[8769]: query[A] fonts.gstatic.com from 192.168.2.131
May 5 11:27:20 dnsmasq[8769]: forwarded fonts.gstatic.com to 127.10.10.2
May 5 11:27:20 dnsmasq[8769]: reply fonts.gstatic.com is <CNAME>
May 5 11:27:20 dnsmasq[8769]: reply gstaticadssl.l.google.com is 172.217.20.99
May 5 11:27:20 dnsmasq[8769]: query[A] lh5.googleusercontent.com from 192.168.2.131
May 5 11:27:20 dnsmasq[8769]: cached lh5.googleusercontent.com is <CNAME>
May 5 11:27:20 dnsmasq[8769]: forwarded lh5.googleusercontent.com to 127.10.10.2
May 5 11:27:20 dnsmasq[8769]: reply lh5.googleusercontent.com is <CNAME>
May 5 11:27:20 dnsmasq[8769]: reply googlehosted.l.googleusercontent.com is 172.217.17.33
pihole-FTL forwards the request to unbound (127.10.10.2), unless of course the entry is cached OR blocked
You can also capture the DNS requests on the raspberry pi, by using the command sudo tcpdump -s0 -w /home/pi/pi.cap. The resulting file can be opened with wireshark, but it will also contain all the DNS requests unbound is making to resolve the DNS request, witch will make it much harder to read and match the chromecast requests to the pihole requests.