I see what you are after, but let me explain what the technical background is, so you know what I'm talking about.
Currently, FTL implements what we think is the bast approach to scan the asynchronous log written by dnsmasq:
Once we find a query entry, we look for the next line that contains (a) the domain name that was just requested and (b) contains the information if it was forwarded, answered from cache, etc. Hence, in this case, FTL determines the status cached in your case and any latter forwardes is ignored.
In the case you are seeing, we could potentially only remember that there was a cached reply and always seek for a forwarded reply nevertheless, however, there is nothing that guarantees us that this forwarded we find actually belongs to the very same query.
Example log snippet where this would work (similar to yours):
...
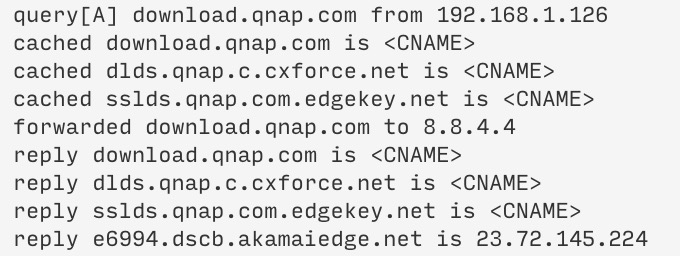
12:00:00 query[A] download.com from 1.2.3.4
12:00:00 cached download.com is <CNAME>
12:00:00 cached abc.download.com is <CNAME>
12:00:01 forwarded download.com to 8.8.4.4
12:00:01 reply download.com is <CNAME>
...
With the new scheme we would recognize that it was cached, but we would also find the forwarded entry, so we could show the query as forwarded.
Another example (assume it would not be forwarded, but the cache would still be valid in the first query):
...
12:00:00 query[A] download.com from 1.2.3.4
12:00:00 cached download.com is <CNAME>
12:00:00 cached abc.download.com is <CNAME>
...
14:00:00 query[A] download.com from 1.2.3.4
14:00:00 forwarded download.com to 8.8.4.4
14:00:00 reply download.com is <CNAME>
...
Here, we would skip the first (correct) cached entry and would find the forwarded that appeared in the logt later.
The general problem comes down to that we are not able to identify which answer belongs to which query. We implement the best analysis we could come up with but it has some intrinsic weak spots. As @DanSchaper already pointed out, more modern versions of dnsmasq actually allow to add IDs into the log file which would allow unambiguous identification of requests and answers but the problem is that out software implementation has to stay general enough to also work with legacy OSs.
![]()